


A vulnerability in Whisper Android Application allowed an attacker to bypass pin and access protected views. The post explains the detection of the vulnerability using Mobile Security Framework - MobSF and exploitation using a custom APK.
Last week I was doing some testing with Mobile Security Framework on some random APKs. In this post, I will talk about one issue that was identified in Whisper Android Application.
The following is the screenshot of Static Analysis Report form Mobile Security Framework.
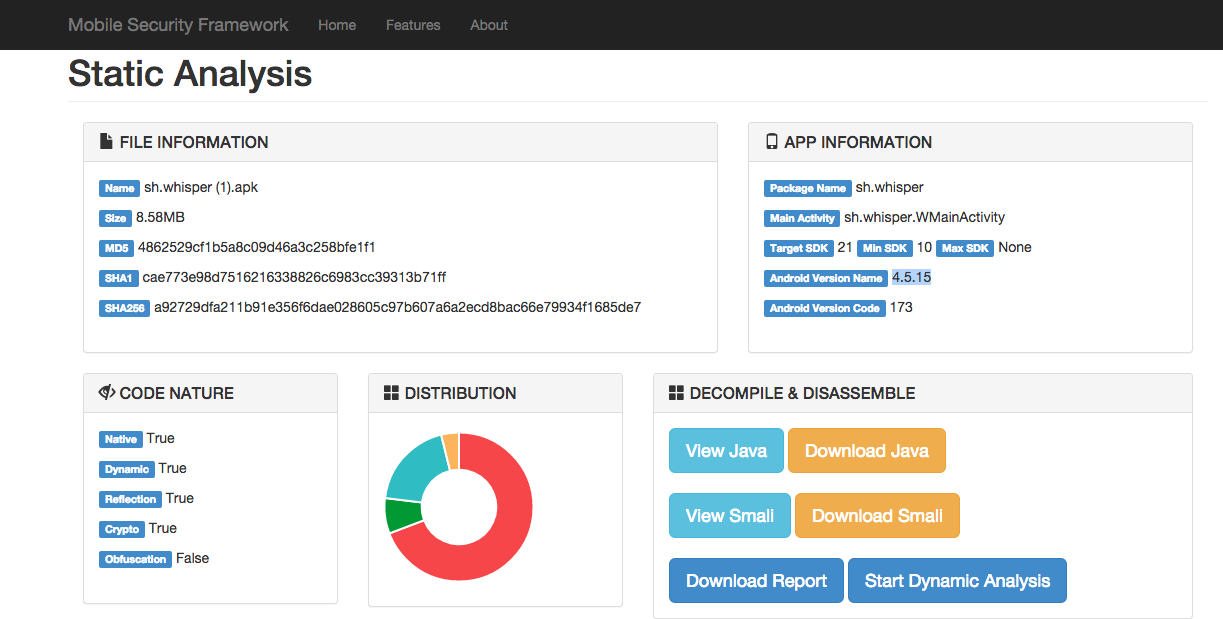
From the Manifest Analysis Section, It was found that lot of Activities where exported.
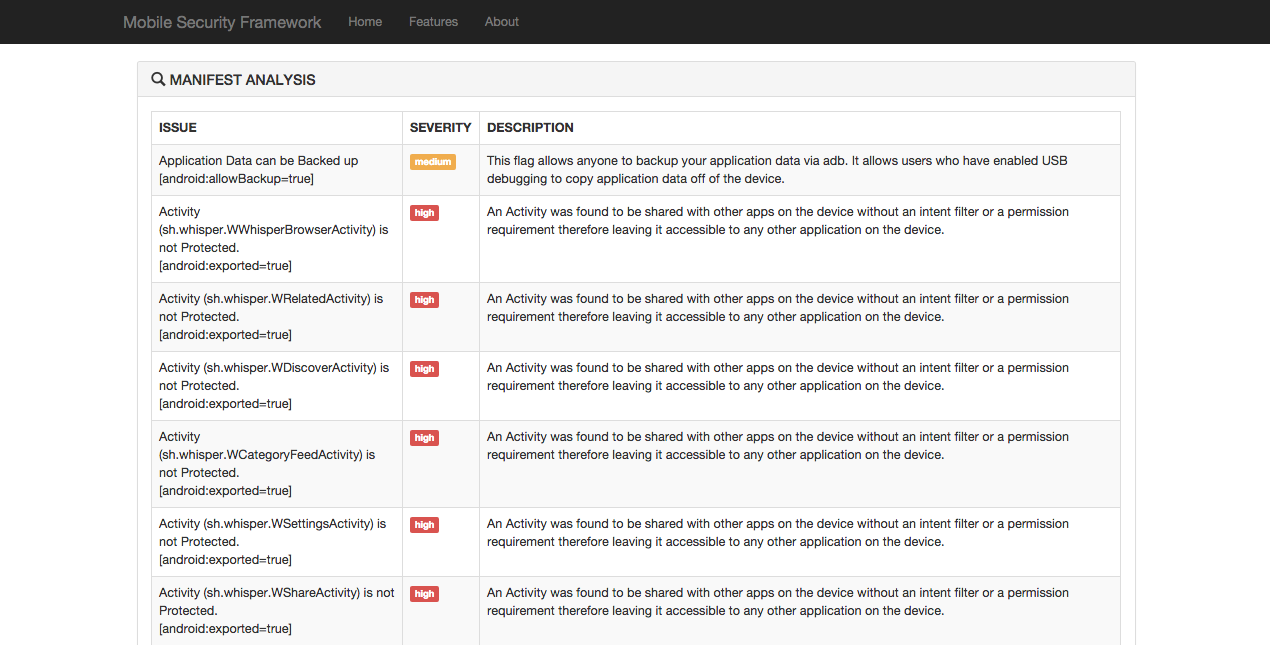
For Android Applications, activities are nothing but the GUI view of the application at an instance. If activities are exposed that means any other applications running in the device can invoke these activities provided, proper permissions are not set on them. If android:exported attribute of an activity is set to true in AndroidManifest.xml, then that means the activity is exported.
Following where the Exported Activities.
sh.whisper.WWhisperBrowserActivity
sh.whisper.WRelatedActivity
sh.whisper.WDiscoverActivity
sh.whisper.WCategoryFeedActivity
sh.whisper.WSettingsActivity
sh.whisper.WShareActivity
sh.whisper.WQuickCreateActivity
sh.whisper.WUserActivity
sh.whisper.WNotificationsActivity
sh.whisper.WInboxActivity
sh.whisper.WAddGroupActivity
Exported Attribute set to true in AndroidManifest.xml
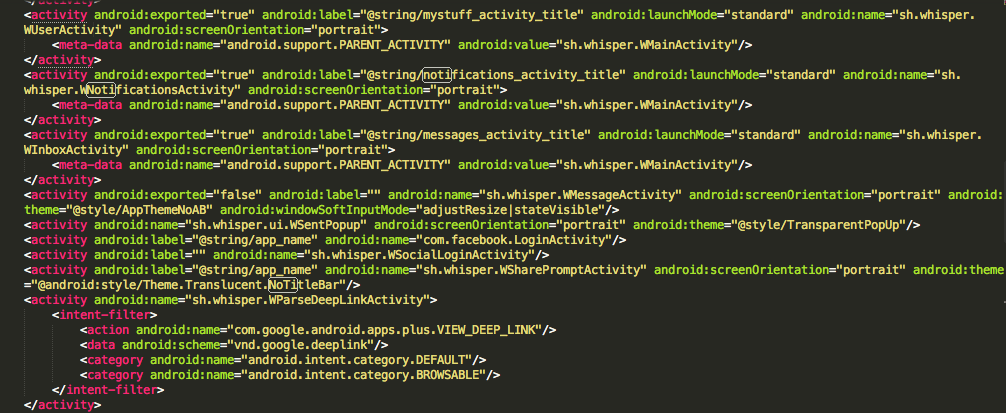
The Whisper application is having a feature to set a PIN to protect unauthorised users from viewing the notification, message etc. Since the activity that corresponds to Messages (sh.whisper.WInboxActivity) and Notifications (sh.whisper.WNotificationsActivity) are exported, we can bypass the PIN functionality by invoking these activities form another application.
I quickly coded up a PoC app that can bypass Whisper PIN.
Download PoC from here: PoC-Whisper.apk
Download vulnerable Whisper APK here: sh.whisper.apk
Mobile Security Framework is an intelligent, all-in-one open source mobile application (Android/iOS) automated pen-testing framework capable of performing static and dynamic analysis. We’ve been depending on multiple tools to carry out reversing, decoding, debugging, code review, and pen-test and this process requires a lot of effort and time. YSO Mobile Security Framework can be used for effective and fast security analysis of Android APK/Android app source code/iOS app source code.
Download it from : GitHub
NOTE:
This issue was disclosed to Whisper Security Team and received a response that it’s a known issue.
Ajin Abraham is a Security Engineer with 10+ years of experience in Application Security, Research and Engineering. He is passionate about building and maintaining open source security tools and communities. Some of his contributions to Hacker's arsenal include Mobile Security Framework (MobSF), nodejsscan, OWASP Xenotix, etc. Areas of interest include runtime security instrumentation, offensive security, web and mobile application security, code and architectural reviews, cloud-native runtime security, security tool development, security automation, breaking and fixing security products, reverse engineering, and exploit development.