


This blog intends to demonstrate how easy it is for anyone with a NFC enabled camera phone to steal card details including CVV/CVC from contactless Credit/Debit/Prepaid cards in seconds.
While spending my lonely social distancing time amid the COVID-19 pandemic, it occurred to me why not write a security blog about something that affects everyone's life. Most of you might have Credit/Debit cards with contactless payment feature. Look for following symbol in your card to know if your card is contactless ready.


These cards use near field communication (NFC) technology so that you can make payments by tapping or placing your card too close to the point of sale (POS) machines. This post is more of a demonstration of how easy it is for rouge actors to abuse the contactless feature in your card to quickly steal card details like Card number, Expiry date and CVV/CVC. Anyone with an android phone having NFC hardware can steal your card information in a matter of seconds if they have access to your card.
Well if they have your card, they could do anything you might ask. While that is true, I will show how you can get scammed in genuine instances like doing a day to day transaction at your grocery store or filling petrol at a gas station where the service is offered by an individual etc.
There are lot of ways your card details can be stolen. Skimming tools like these steal data from the magnetic stripe of your card.  Then there are portable devices like a mini POS that can handle contactless payment, which can be abused by a rouge actor like for example. Knowing this possible abuse, most POS machines offered to merchants have a limit on how much you can pay via contactless mode on a single tap like an upper limit of 100$ in some countries. For transaction above these limits, you might have to insert the card into the POS machine and manually enter the pin. The data captured from the card via this method will not have the static CVV/CVC that's printed behind most cards. For an attacker, your Card number, Expiry date and CVV are the most valuable information along with Name/ZIP code in some countries. We will see how one can steal these information with an NFC enabled android phone in the coming section.
Then there are portable devices like a mini POS that can handle contactless payment, which can be abused by a rouge actor like for example. Knowing this possible abuse, most POS machines offered to merchants have a limit on how much you can pay via contactless mode on a single tap like an upper limit of 100$ in some countries. For transaction above these limits, you might have to insert the card into the POS machine and manually enter the pin. The data captured from the card via this method will not have the static CVV/CVC that's printed behind most cards. For an attacker, your Card number, Expiry date and CVV are the most valuable information along with Name/ZIP code in some countries. We will see how one can steal these information with an NFC enabled android phone in the coming section.
For demonstrating how easy it is to steal these information, I made up a proof of concept Android app that uses Android's NFC and Google Vision APIs. The following digram explains the working of this proof of concept.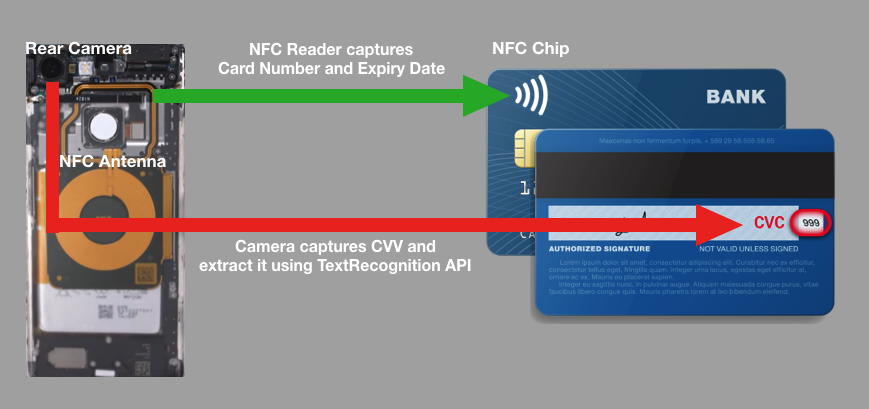
NFC API allows you to capture Card number, Card issuer and Expiry date using NFC hardware in the phone. The 3 digit static CVV/CVC on the back of the card is captured using Vision Text Recognition API. I will not be releasing the source code/binary due to possible ease of abuse. It took me only 5 hours to build this proof of concept, so it’s not that difficult either.
I have used my real cards for this proof of concept and hence masked them physically as well as masked the sensitive information inside the PoC application.
This is probably already well established with cyber criminals. This demo video is to educate you so that you will be more vigilant the next time you handover your card for a transaction. This is no vulnerability but a feature abuse, so being cautious is the best way to prevent your card details from being stolen. In some countries like India, it is common to have a second factor authentication like a one time password (OTP) that is sent over SMS when you perform an online transaction with your card. This can prevent possible fraud locally within the country, but it's not applicable outside the country as international online transactions does not require an OTP. There is a new technology called Dynamic CVV that will address this problem to some extent. Cards with Dynamic CVV will have a tiny electronic ink display that changes CVV number at fixed intervals like time based OTP.
Ajin Abraham is a Security Engineer with 10+ years of experience in Application Security, Research and Engineering. He is passionate about building and maintaining open source security tools and communities. Some of his contributions to Hacker's arsenal include Mobile Security Framework (MobSF), nodejsscan, OWASP Xenotix, etc. Areas of interest include runtime security instrumentation, offensive security, web and mobile application security, code and architectural reviews, cloud-native runtime security, security tool development, security automation, breaking and fixing security products, reverse engineering, and exploit development.